Download and Install the tools you need to collaborate with your colleagues and/or students. View or Download the Collaboration Tools Handout for a quick overview of all the tools you have available or get started below. In addition, our Free Tools page offers all of the free tools and resources that we have collected to help you during this season of being remote.
Canvas
Primary Use: CSN’s Learning Management System, view content, turn in assignments, take quizzes/exams, and communicate with instructors and other students
- Log in
- Canvas Student Guide: https://community.canvaslms.com/docs/DOC-10701-canvas-student-guide-table-of-contents
- Install Mobile App: https://community.canvaslms.com/docs/DOC-4048-mobile-guides-canvas-student
- Canvas Frequently Asked Questions
Big Blue Button
Primary Use: A built-in tool with Canvas for video conferencing with students.
Respondus LockDown Browser
LockDown Browser® is a custom browser that locks down the testing environment within a learning management system.
ProctorU
Primary Use: Online exam proctoring application.
Check your device for compatibility: ProctorU Requirements
Install ProctorU on a compatible device: ProctorU Download
Microsoft 365
Primary Use: All of the Microsoft collaborations tools, specifically Email, Office, Teams, and Stream.
- About Teams
- Log in and click the Email Tile
- Explore tutorials and how-to documents on Enhance your skills tab
- Install Microsoft Office 365 (Desktop or Mobile): Office 365 Download
- Install Microsoft Teams (Desktop or Mobile): https://products.office.com/en-us/microsoft-teams/download-app
- Microsoft 365 Frequently Asked Questions
Webex Meetings
Primary Use: Video conferencing tool for meeting with colleagues and students.
- Install Browser add-on
- Webex Meetings Frequently Asked Questions
Still Need Help
www.csn.edu/helpdesk
Local: 702-651-HELP (4357)
Toll-Free: 800-630-7563
OTS Web Site: https://at.csn.edu/ots
CSN Call Center
Voice: 702-651-5555
Find a quiet place for online classes
Try to find a quiet space where you won’t be interrupted. Ensure you have good lighting and wear headphones to help you focus on the online session.
Share your virtual class schedule
Speaking of quiet areas, work out a schedule with your family or roommates for class time. Young children may be home from school, and many parents are working remotely from the house too. Limit distractions as much as possible by planning your class time with everyone at home.
You may be sharing internet bandwidth as well. Let your housemates know when you need to attend class online. Ask others to limit streaming apps and large downloads while you’re attending class. It’s a tough ask while we’re all working and studying from home — we know!
Test your system
When you’re invited to an online session, the email usually includes a link to test your computer, tablet, or phone to ensure the video conferencing solution will work. Don’t forget to check your device the day before class, so you’ll have time to address any technical issues. It’s helpful to ensure you can log on to sessions using a mobile data connection, in case your Internet service is slow or interrupted.
Also, most video conferencing systems have chat and Q&A options. Ask your class leader ahead of time which option to use to submit questions and comments.
You can test by doing the following:
- Webex Meetings: Go to https://www.webex.com/test-meeting.html and enter your name, email, and click join now.
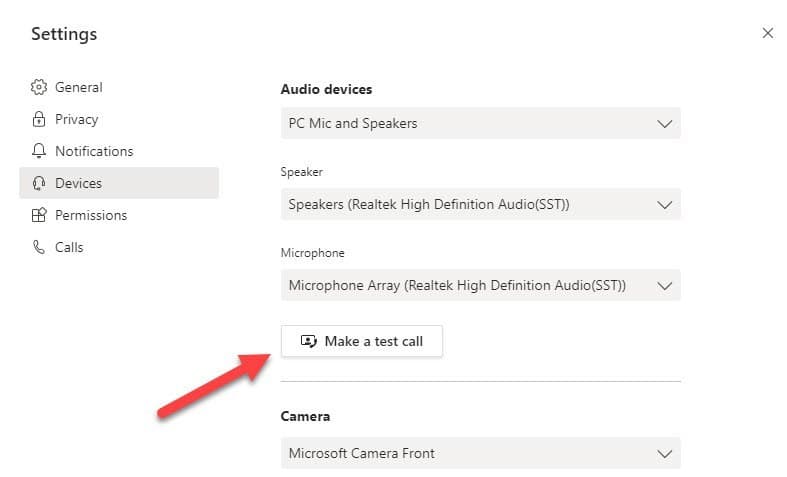
- Microsoft Team Meetings: To make a test call with the desktop client, click your avatar (picture) in the top bar and select Settings, then Devices. Make sure that the right audio devices are selected for the test and then click Make a test call.
Also, if you use any online accessibility tools for visual or hearing impairments, test that those work with your online class platform too. Ask your teacher to set up a test session if needed.
Complete assignments and download materials before class
Get familiar with the material and complete any assigned reading so you can follow along during the lesson and ask questions. Let your teacher know if you had any issues accessing materials.
Mute your cell phone during class
Turn off your ringer and vibrate function to avoid the temptation to pick up your mobile phone. Remember to pause all text and app notifications to limit distractions. Better yet, turn your phone off unless you’re using it to attend class.
Mute the mic on your device
Mute your device microphone when not speaking during a video conferencing class. Muting the mic will limit the noise others will hear. Make sure you know how to mute your microphone before class begins.
Remember it’s a real class
Keep in mind this is a real class, and you will be graded. Pay attention to the lectures, and do your assignments. Finally, deadlines are still deadlines. Complete your work on time and respect your fellow students’ and educators’ time during online classes.
Security Awareness Training when Working From Home
Home may be the best place to work during a health crisis. But the chances of your information getting compromised is also higher. This animation shows an example of what can go wrong and provides specific tips to stay safe.
From: https://ermprotect.com/unlocked-security-awareness-training
Phishing
Phishing is a technique that hackers use to get people to click on malicious links that give them access to sensitive information. In a crisis, they might send fake emails from government or health care providers. This animation shows an example of what can go wrong and provides specific tips to stay safe.
Phishing attacks are delivered via email. Most commonly, a phishing email uses a sense of urgency to direct the victim to visit a website designed to steal the victim's account credentials. Some phishing attacks are straightforward, for example, "Update your password now!!!!" and can easily be detected because they typically are not written well (poor grammar and word choice). However, some attacks are sophisticated, look like they come from a trusted contact, are well written, and lead to a site that closely resembles the spoofed website. If you receive a communication that asks you to give your account credentials or personal information (for example, your social security number, birth date, or credit card number), DO NOT click the email link. Instead, go directly to the expected website and verify that the communication came from that organization. Always check with your IT department before following links that require you to enter your username and password. By following these simple precautions and working with your IT department, we can make phishing attacks a thing of the past.
Social Engineering
Social engineering begins with research, whereby an attacker reaches out to a target to gain information and resources. When someone you don't know contacts you and asks you open-ended questions, this may be the first step of a social-engineering attack. After the attacker reaches out to you, they will then attempt to establish trust with you and get you to provide them with the information or access that they need. Often, the attacker does this by creating a sense of urgency. One common social-engineering scam is the gift-card scam. The attacker poses as an executive. The "executive" will email the victim, ask if the victim is in the office, and begin a brief email exchange with the victim. The executive will tell the victim that they need to purchase one or more gift cards for other employees but that they are unavailable to do so. The executive will ask the victim to buy several gift cards and keep one for themselves. As the victim is worried about pleasing the executive, the victim goes through with the purchase, spending hundreds or thousands of dollars. How do you avoid becoming a victim of these types of attacks? Ask yourself if the request makes sense. Check the email address of the sender. Does the sender's email address include an extension that you would expect (.edu, for example)? Whenever you receive an "urgent" email communication, the first thing you should do is contact the sender using another mode, such as phone or text message, and confirm that the email is legitimate. If something seems off to you, it probably is.
Ransomware
Ransomware is scary. Such an attack could make it impossible for you to retrieve documents on your computer. So, how do you protect yourself from ransomware? One of the best ways to protect yourself is to create a good backup of your critical data. These backups should be available offline, for example, on a removable hard drive. Having multiple backups that are stored in more than one location is best! For your work files, be sure to follow guidelines from your IT department. Ransomware is often delivered via a fraudulent email with an attachment or link that, when clicked, installs a program that locks your files. Never open an attachment that you are not expecting without verifying with the source in another way (for example, via phone or text message) that the attachment is valid. When you are unsure, follow guidance from your IT department regarding how to handle questionable emails. Using these common-sense practices can help you avoid the pain of a successful ransomware attack.
From: https://er.educause.edu/blogs/2020/3/march-2020-making-phishing-attacks-history
Digital Wellbeing and Mental Health
In this unprecedented time, technology has become part of the social fabric in a deeper, more intimate way than ever before—for those of us able to access it, technology has been a social lifeline. Unfortunately, our increased reliance on technology doesn’t diminish the challenges and dangers it poses. It is important that we all adhere to recommended guidelines in the hope that they will help students, faculty & staff who are feeling overwhelmed trying to navigate the amount of technology used in our daily lives. To make technology more of a tool for well-being, rather than a hindrance. It is also important to remember that many of the applications we might already be accustomed to are not as beneficial as we may think. The social media platforms that many of us use everyday are designed to keeping us scrolling, clicking, and watching. The result is a system that creates addiction, self-obsession, misinformation, and content that outrages and polarizes. In recognition of mental health month, check out these ready-made pieces of content designed to enhance security, privacy, and for this month mental health awareness. Use these tips and resources to better your digital wellbeing.
From: May 2020: Digital Wellbeing and Mental Health during a Pandemic and Beyond
Download and Install the tools you need to collaborate with your colleagues and/or students. View or Download the Collaboration Tools Handout for a quick overview of all the tools you have available or get started below. In addition, our Free Tools page offers all of the free tools and resources that we have collected to help you during this season of being remote.
Canvas
Primary Use: CSN’s Learning Management System, view content, turn in assignments, take quizzes/exams, and communicate with instructors and other students
- Log in
- Canvas Student Guide: https://community.canvaslms.com/docs/DOC-10701-canvas-student-guide-table-of-contents
- Install Mobile App: https://community.canvaslms.com/docs/DOC-4048-mobile-guides-canvas-student
- Canvas Frequently Asked Questions
Big Blue Button
Primary Use: A built-in tool with Canvas for video conferencing with students.
Respondus LockDown Browser
LockDown Browser® is a custom browser that locks down the testing environment within a learning management system.
ProctorU
Primary Use: Online exam proctoring application.
Check your device for compatibility: ProctorU Requirements
Install ProctorU on a compatible device: ProctorU Download
Microsoft 365
Primary Use: All of the Microsoft collaborations tools, specifically Email, Office, Teams, and Stream.
- About Teams
- Log in and click the Email Tile
- Explore tutorials and how-to documents on Enhance your skills tab
- Install Microsoft Office 365 (Desktop or Mobile): Office 365 Download
- Install Microsoft Teams (Desktop or Mobile): https://products.office.com/en-us/microsoft-teams/download-app
- Microsoft 365 Frequently Asked Questions
Webex Meetings
Primary Use: Video conferencing tool for meeting with colleagues and students.
- Install Browser add-on
- Webex Meetings Frequently Asked Questions
Still Need Help
www.csn.edu/helpdesk
Local: 702-651-HELP (4357)
Toll-Free: 800-630-7563
OTS Web Site: https://at.csn.edu/ots
CSN Call Center
Voice: 702-651-5555
Find a quiet place for online classes
Try to find a quiet space where you won’t be interrupted. Ensure you have good lighting and wear headphones to help you focus on the online session.
Share your virtual class schedule
Speaking of quiet areas, work out a schedule with your family or roommates for class time. Young children may be home from school, and many parents are working remotely from the house too. Limit distractions as much as possible by planning your class time with everyone at home.
You may be sharing internet bandwidth as well. Let your housemates know when you need to attend class online. Ask others to limit streaming apps and large downloads while you’re attending class. It’s a tough ask while we’re all working and studying from home — we know!
Test your system
When you’re invited to an online session, the email usually includes a link to test your computer, tablet, or phone to ensure the video conferencing solution will work. Don’t forget to check your device the day before class, so you’ll have time to address any technical issues. It’s helpful to ensure you can log on to sessions using a mobile data connection, in case your Internet service is slow or interrupted.
Also, most video conferencing systems have chat and Q&A options. Ask your class leader ahead of time which option to use to submit questions and comments.
You can test by doing the following:
- Webex Meetings: Go to https://www.webex.com/test-meeting.html and enter your name, email, and click join now.
- Microsoft Team Meetings: To make a test call with the desktop client, click your avatar (picture) in the top bar and select Settings, then Devices. Make sure that the right audio devices are selected for the test and then click Make a test call.
Also, if you use any online accessibility tools for visual or hearing impairments, test that those work with your online class platform too. Ask your teacher to set up a test session if needed.
Complete assignments and download materials before class
Get familiar with the material and complete any assigned reading so you can follow along during the lesson and ask questions. Let your teacher know if you had any issues accessing materials.
Mute your cell phone during class
Turn off your ringer and vibrate function to avoid the temptation to pick up your mobile phone. Remember to pause all text and app notifications to limit distractions. Better yet, turn your phone off unless you’re using it to attend class.
Mute the mic on your device
Mute your device microphone when not speaking during a video conferencing class. Muting the mic will limit the noise others will hear. Make sure you know how to mute your microphone before class begins.
Remember it’s a real class
Keep in mind this is a real class, and you will be graded. Pay attention to the lectures, and do your assignments. Finally, deadlines are still deadlines. Complete your work on time and respect your fellow students’ and educators’ time during online classes.
Security Awareness Training when Working From Home
Home may be the best place to work during a health crisis. But the chances of your information getting compromised is also higher. This animation shows an example of what can go wrong and provides specific tips to stay safe.
From: https://ermprotect.com/unlocked-security-awareness-training
Phishing
Phishing is a technique that hackers use to get people to click on malicious links that give them access to sensitive information. In a crisis, they might send fake emails from government or health care providers. This animation shows an example of what can go wrong and provides specific tips to stay safe.
Phishing attacks are delivered via email. Most commonly, a phishing email uses a sense of urgency to direct the victim to visit a website designed to steal the victim's account credentials. Some phishing attacks are straightforward, for example, "Update your password now!!!!" and can easily be detected because they typically are not written well (poor grammar and word choice). However, some attacks are sophisticated, look like they come from a trusted contact, are well written, and lead to a site that closely resembles the spoofed website. If you receive a communication that asks you to give your account credentials or personal information (for example, your social security number, birth date, or credit card number), DO NOT click the email link. Instead, go directly to the expected website and verify that the communication came from that organization. Always check with your IT department before following links that require you to enter your username and password. By following these simple precautions and working with your IT department, we can make phishing attacks a thing of the past.
Social Engineering
Social engineering begins with research, whereby an attacker reaches out to a target to gain information and resources. When someone you don't know contacts you and asks you open-ended questions, this may be the first step of a social-engineering attack. After the attacker reaches out to you, they will then attempt to establish trust with you and get you to provide them with the information or access that they need. Often, the attacker does this by creating a sense of urgency. One common social-engineering scam is the gift-card scam. The attacker poses as an executive. The "executive" will email the victim, ask if the victim is in the office, and begin a brief email exchange with the victim. The executive will tell the victim that they need to purchase one or more gift cards for other employees but that they are unavailable to do so. The executive will ask the victim to buy several gift cards and keep one for themselves. As the victim is worried about pleasing the executive, the victim goes through with the purchase, spending hundreds or thousands of dollars. How do you avoid becoming a victim of these types of attacks? Ask yourself if the request makes sense. Check the email address of the sender. Does the sender's email address include an extension that you would expect (.edu, for example)? Whenever you receive an "urgent" email communication, the first thing you should do is contact the sender using another mode, such as phone or text message, and confirm that the email is legitimate. If something seems off to you, it probably is.
Ransomware
Ransomware is scary. Such an attack could make it impossible for you to retrieve documents on your computer. So, how do you protect yourself from ransomware? One of the best ways to protect yourself is to create a good backup of your critical data. These backups should be available offline, for example, on a removable hard drive. Having multiple backups that are stored in more than one location is best! For your work files, be sure to follow guidelines from your IT department. Ransomware is often delivered via a fraudulent email with an attachment or link that, when clicked, installs a program that locks your files. Never open an attachment that you are not expecting without verifying with the source in another way (for example, via phone or text message) that the attachment is valid. When you are unsure, follow guidance from your IT department regarding how to handle questionable emails. Using these common-sense practices can help you avoid the pain of a successful ransomware attack.
From: https://er.educause.edu/blogs/2020/3/march-2020-making-phishing-attacks-history
Digital Wellbeing and Mental Health
In this unprecedented time, technology has become part of the social fabric in a deeper, more intimate way than ever before—for those of us able to access it, technology has been a social lifeline. Unfortunately, our increased reliance on technology doesn’t diminish the challenges and dangers it poses. It is important that we all adhere to recommended guidelines in the hope that they will help students, faculty & staff who are feeling overwhelmed trying to navigate the amount of technology used in our daily lives. To make technology more of a tool for well-being, rather than a hindrance. It is also important to remember that many of the applications we might already be accustomed to are not as beneficial as we may think. The social media platforms that many of us use everyday are designed to keeping us scrolling, clicking, and watching. The result is a system that creates addiction, self-obsession, misinformation, and content that outrages and polarizes. In recognition of mental health month, check out these ready-made pieces of content designed to enhance security, privacy, and for this month mental health awareness. Use these tips and resources to better your digital wellbeing.
From: May 2020: Digital Wellbeing and Mental Health during a Pandemic and Beyond